What is a ‘Cybernetic Avatar’, (CA)?
The term ‘Cybernetic Avatar’ is a combination of the words ‘Cybernetics’ and ‘Avatar’.
The term ‘Cybernetics’ is said to be derived from the Ancient Greek term ‘kybernetikos’, (Κυβερνήτης).
(Stuart Umpleby, Definitions of Cybernetics, American Society of Cybernetics <https://asc-cybernetics.org/definitions/>(1982; revised 2000).)
(Fumio Shimpo, ‘Authentication of Cybernetic Avatars and Institutional Challenges – Based also on the Development Concept of New Dimension Area Jurisprudence’, Journal of the Robotics Society.

It is thought that the term was first used by the French physicist André-Marie Ampère in the first half of the 19th century, in his treatise on ‘The Governance of Administrative Districts’, in which he attempted ’to derive a general law of control by considering control as a purely abstract thing, detached from its object’. (Saburo Akabori, ‘Post-war governance’.
(Saburo Akabori, ‘Cybernetics and Sociology in Postwar America’, Economy and Society (Bulletin of the Sociological Society of Tokyo Women’s University), vol. 37 (2009), p. 30.)
Ampere was the physicist who formulated Ampere’s Law, which showed the relationship between electrical current and magnetic fields; the ampere, being the unit of measurement for electrical current named after the physicist,which is so familiar to us in our daily lives.
(Norbert Wiener, Cybernetics: or Control and Communication in the Animal and the Machine. Cambridge, Massachusetts, MIT Press (1948).)
After this, in 1948, the American mathematician Norbert Wiener used the term in his book ‘Cybernetics’, which became widely known to the public.
(Norbert Wiener, Cybernetics: or Control and Communication in the Animal and the Machine. Cambridge, Massachusetts, MIT Press (1948))
The word ‘avatar’ derives from the Sanskrit word ‘avatāra’, (अवतार, Avatāra) of Lord Vishnu. Avatāra means ‘incarnation’.
The term ‘avatar’ is currently used to mean the ‘alter ego’ of ‘oneself’. However, its original meaning is that of the ‘alter egos, (incarnation) of the Hindu and Buddhist Gods’; and not the alter egos of humans, (natural persons).
(Fumio Shimpo, ‘Proof of the Existence of the Cybernetic Avatar’,).

Objectives of the R&D Project
Currently, Cybernetic Avatars are used without the CA being able to recognise ‘who’ the avatar is, which can be unworkable. Therefore, avatars are not seen as trustworthy entities in society. As a result, it would be difficult to utilise CA’s in activities such as contracts and negotiations.
It follows therefore that, in order to use CA’s safely, securely and reliably in daily life, the aim of this research and development project must be to study and establish a ‘CA Certification’ mechanism to guarantee their reliability.
Overview of Research and Development Project
This research and development project examines the results of ‘SOCIO-CA’ and ‘In-Body CA’ use, which it is hoped, will be used in society to free people from the constraints of body, brain, space and time; the latter being able to operate within the body. This research will also clarify the technical and institutional issues common to the different CA’s currently available, and will make proposals for solving the domestic and international technical and institutional issues. Accordingly, regarding the domestic issues, a forum for gathering the opinions of citizens will be established. By this means, the research project team will build a CA infrastructure which will ensure safety, security and trust, and will enhance social acceptability.
By building an ‘Infrastructure for Ensuring the Safety and Security of CA Use’, the project will contribute to the promotion of Target 1, ‘CA Infrastructure’, of the Moonshot Project Objective 1. At the same time, by promoting research on ethical, economic, environmental, legal and social issues, ‘E3LSI’, we will conduct research to realise Target 2, ‘Propose a New Way of Life based on Socially Accepted Ideas’.
Supplying a Vision of Society via Achieving the Aims of the Research and Development Project.
The first aim is to realise an infrastructure for ensuring CA safety and security via user authentication, CA certification and CA notarisation. By building this infrastructure, we aim to ensure safety, security and reliability, and to increase the social acceptability of CA’s, thereby creating a world in which CA’s become alter egos and interact with people, and CA’s interact with each other; in other words, a society in which a totally new form of communication via CA use, is possible.
1-1 Team 1: Inter-Project Collaboration and Demonstration Management
Research and Development Tasks
- R&D Task 1-1: support for collaboration between R&D projects and for demonstration experiments and data collection
Basic Policy
- This team will organise the necessary safety and security assurance issues for SOCIO-CA and In-Body CA use and, in cooperation with Team 2, ‘Construction of CA Safety and Security Assurance Infrastructure’, will conduct the necessary demonstration experiments and will build the database for evaluation in order to construct the CA infrastructure.
- Team 1 will request the other projects, (the SOCIO-CA and In-Body CA teams) to re-consider their R&D agendas, if they have any safety or security concerns.
- The project will identify any R&D issues which need to be researched in an inter-disciplinary manner, under Moonshot Project Objective 1, and will request the relevant R&D.
- The project will identify the institutional issues which need to be addressed in order to be accepted by society, and to formulate and implement measures to resolve these issues within the project.
1-2 Team 2: Building CA Safety and Security Infrastructure
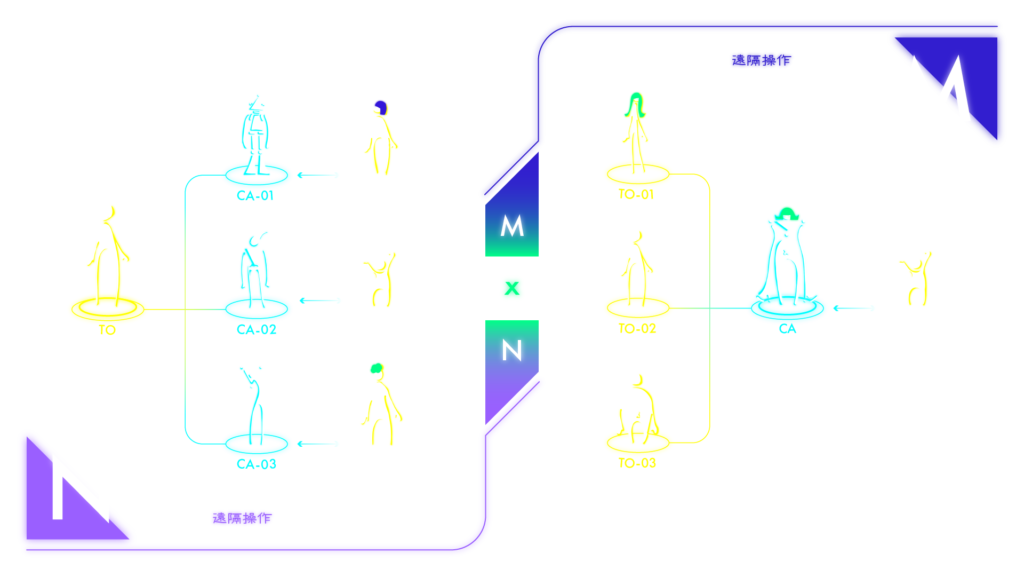
Preventing CA ‘hijacking’, ‘spoofing’ and ‘illegal or illicit imitation of skills’, is essential for the team. Consequently, a CA Safety and Security Assurance Infrastructure will be built to ensure that users, (CA remote operators and CA service users) will be able to receive CA services safely and securely in a society where people and avatars are intricately intertwined and connected.
This CA safety and security assurance infrastructure combines the above-mentioned user authentication, CA authentication and notarisation and is the foundation for a ‘2050 Future Society’, which aims at remote operation and capacity expansion of multiple avatars by multiple people.
Research and Development Tasks
- R&D Task 2-1: Design of Infrastructure to Ensure CA Safety and Security
- R&D Task 2-2: Development of Multi-Modal Short-Term User Authentication and CA Authentication Technology
- R&D Task 2-3: Development of Wireless Fingerprint-Based Short-Term User Authentication and CA Notarisation Technology
- R&D Task 2-4: Development of Technology for CA Notarisation of Short Term and Intangible Objects
- R&D Task 2-5: Development of CA Notarisation Technology for Short Term Tangible Objects
- R&D Task 2-6: Development of Long Term User Authentication, CA Authentication and CA Notarisation Technology
- R&D Task 2-7: Social Implementation of CA Safety and security Infrastructure
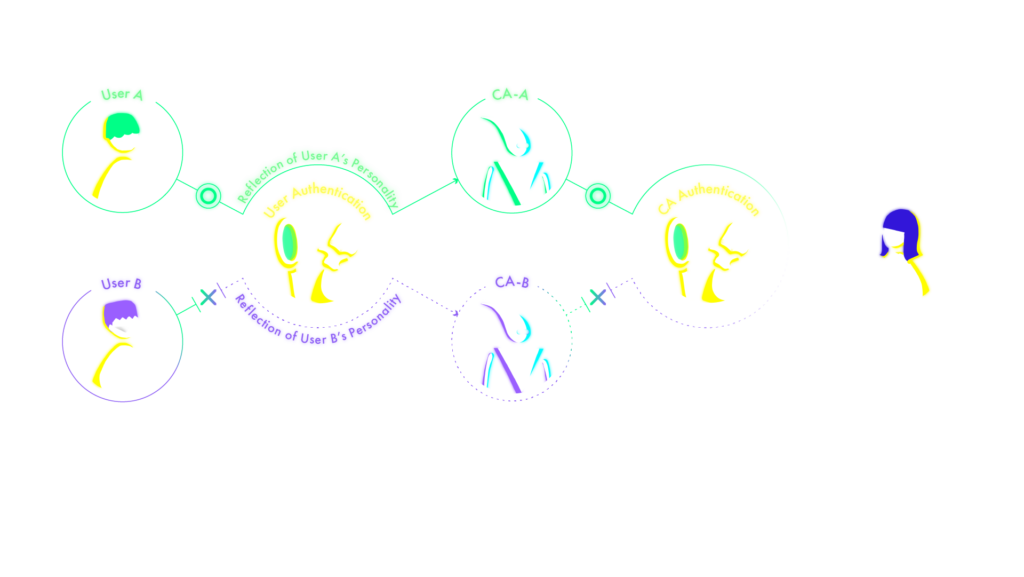
User Authentication
The use of multi-modal biometrics, which is attracting a lot of attention because of its low risk of theft and leakage, will be studied.
The concept of multi-factor authentication will be introduced, which will combine authentication by wireless radio fingerprints, (‘Wireless Fingerprints’) emitted from smartphones, wearable devices, PC’s, etc, used by the user when remotely controlling the CA.
Multi-modal biometrics will become an authentication method which will combine several types of biometric data which are part of the person’s body. It will enable a high level of security, including the prevention of identity theft, and there will be no risk of loss, as is the case with identity cards.
In this project, user authentication at the start of CA use, followed by continuous authentication, assuming CA remote operation, will be referred to as ‘short term user authentication’.
In addition to this, user authentication using lifelog data obtained from observation over a longer period of time, such as 24 hours or a week, will be referred to as ‘long term user authentication’.
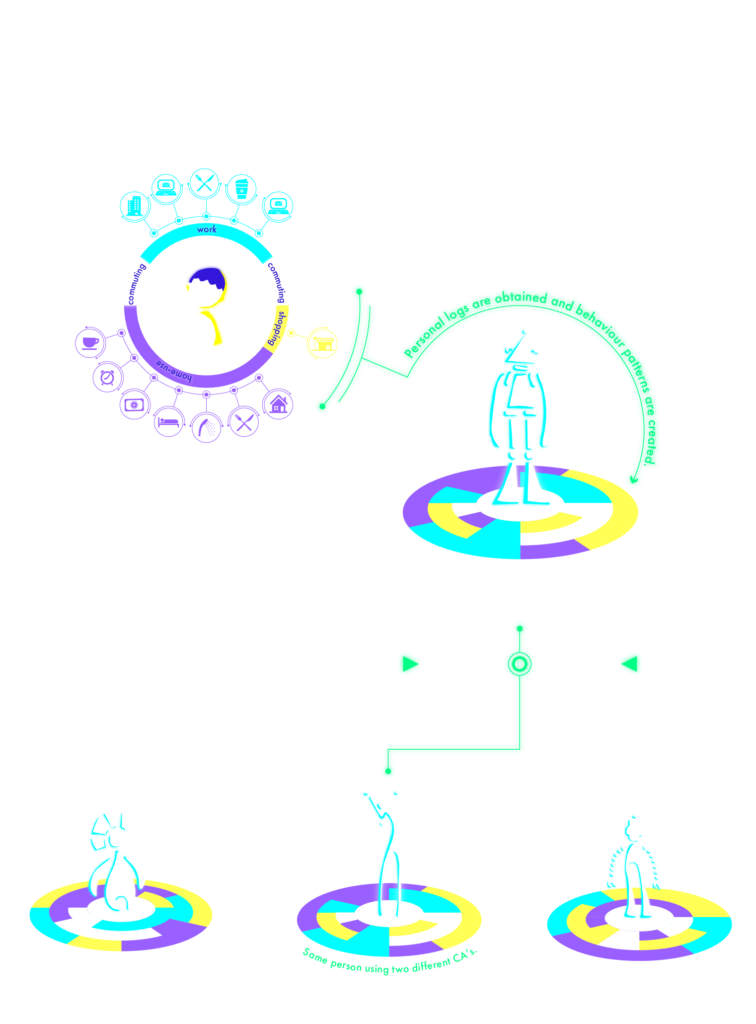
Monitoring using different time scales will increase robustness as a safety and security measure. This user authentication is also considered to be an effective tool in the event of hijacking by unauthorised access during the CA remote control process.
CA Certification
Since the CA acts as the alter-ego of the CA remote operator, it imitates the CA remote operator’s appearance, behaviour, facial expressions and speech, thereby giving the service user a sense of one-ness with it. It follows therefore that there is the possibility of an illegal ‘detection impersonation’ and hijacking by observing the CA as well. This fact therefore re-enforces the need for ‘CA Authentication’ technology.
This project envisages a future society in which multiple operators operate multiple CA’s, with remote control and capability expansion, and develops a control method which has the capability to separate the individuality of multiple remote operators both temporally and spatially, (ie, the body parts and modalities of CA’s) and assigns them adaptively. In addition, there will be a cross-modal CA authentication technology which will recognise multiple remote operators vis-a-vis the individuality referred to above.
CA Notarisation
CA Notarisation is a technique for verifying whether a CA is legitimate or not.
If an Unauthorised CA, (Non-Authorised CA) impersonates an Authorised CA, the information which is displayed by the Non-Authorised CA is different from that of the Authorised CA remote operator, thus preventing impersonation. However, if the functional level of the Authorised CA is low and the Authorised CA cannot operate as required by the CA remote operator, the identity of both the remote operator and the authorised CA may not be guaranteed.
CA Notarisation is a technique which defines the functional level of an Authorised CA and then publicly certifies that level of functionality which the Authorised CA can achieve.

1-3 Team 3: Research on E3LSI and Policy Development
Research and Development Tasks
- R&D Task 3-1: Establishment of E3LSI Research Infrastructure
- R&D Task 3-2: Comprehensive Research on E3LSI Issues related to CA Research, Development and Utilisation
- R&D Task 3-3: Research on Fostering Cybernetic Avatar Methods
- R&D Task 3-4: Intellectual Property Protection and Social and Policy Development of CA’s
- R&D Task 3-5: CA Labour and Economic Activities
- R&D Task 3-6: CA Econometrics
- R&D Task 3-7: Linkage of CA Research and Development Tasks
Basic Policy
- E3LSI issues, (Ethical, Economic, Environmental, Legal, and Social Issues) in the operation of CA safety and security infrastructure to be studied:
- establish a ‘Centre for Cyber-Physical Sustainability’, (CPS Centre); a research centre for the legal protection of sustainable CA’s and new social systems and legal policies to utilise cyber-physical space, and for the drafting and dissemination of the research results which emerge;
- advocate a ‘New Dimension Law’, (AI, Robotics and Avatar Law) and develop this as a new academic discipline;
- focus on social and legal norms for the acceptance of avatars in society and establish legal systems to deal with legal issues when avatars engage in economic activities, (including economic security and dual-use issues).